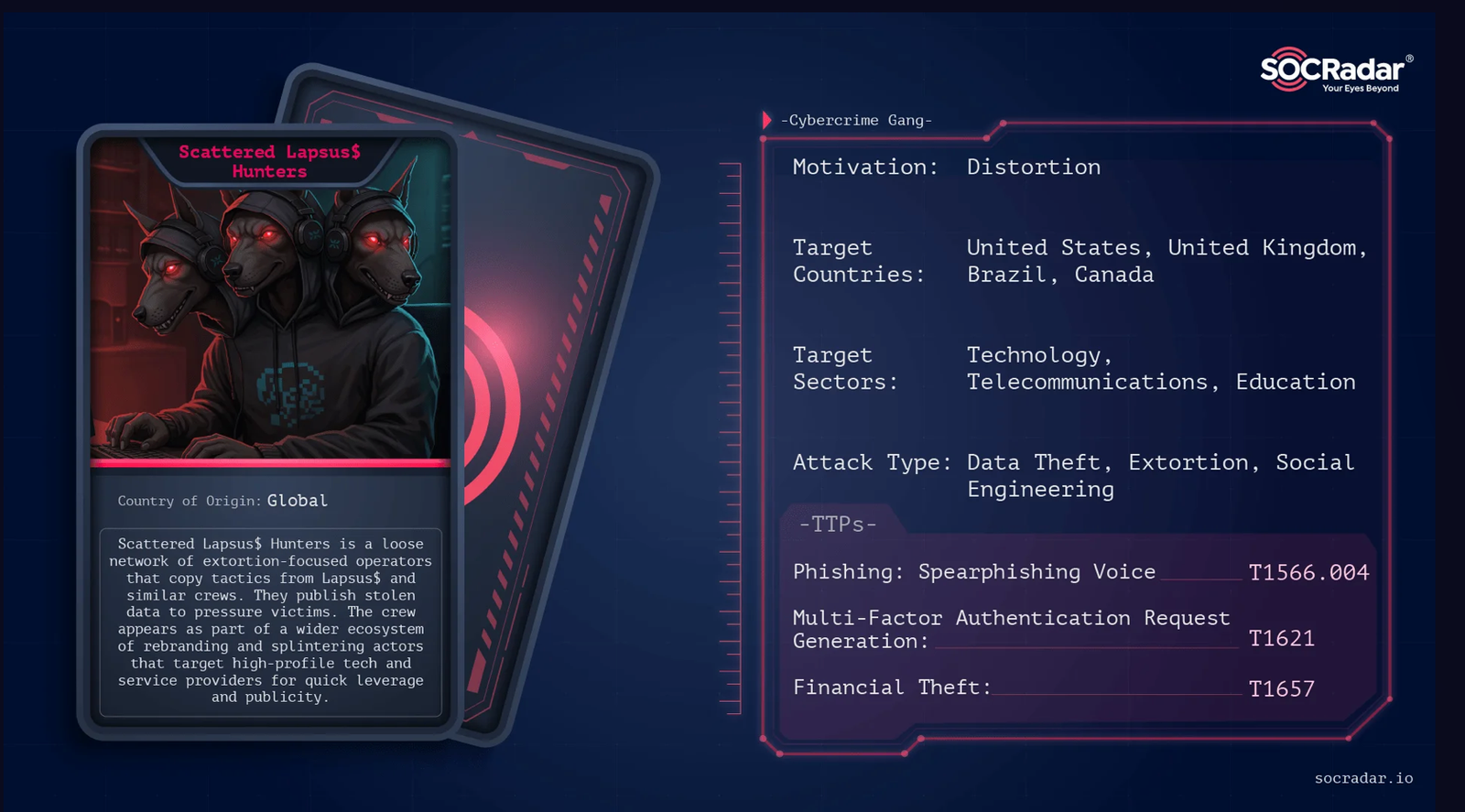
A notorious hacker network with ties to Scattered LAPSUS$ Hunters has released personal data on U.S. law enforcement officers, raising alarms about insider risks, foreign influence, and the safety of agents now publicly exposed.
By Gina Hill | Alaska Headline Living | October 2025
A new wave of doxxing has struck U.S. law enforcement. This week, a hacker group calling itself “The Com” published the names, phone numbers, home addresses, and emails of hundreds of officials from Immigration and Customs Enforcement (ICE), the FBI, and the Department of Justice (DOJ).
Cyber analysts say the leak, first spotted on private Telegram channels, appears to be the work of hackers linked to Scattered LAPSUS$ Hunters, a decentralized collective known for high-profile breaches and data dumps designed to embarrass governments and corporations.
How They Did It
While investigators have not confirmed how the data was obtained, experts believe it was likely compiled through a combination of phishing, insider access, and data aggregation from older leaks, rather than a single large system hack. The group’s Telegram activity shows patterns of social engineering and possible infiltration of government contractors who handle personnel records.
“It’s less about a zero-day exploit and more about persistence and manipulation,” one cybersecurity analyst told 404 Media. “They’re very good at convincing insiders to open doors.”
Why They Say They Did It
Posts in the hacker channels claim the dump was partly “retaliation” for U.S. immigration enforcement. Some messages referenced rumors that Mexican cartels have offered bounties for doxxing or harming U.S. agents, though the Department of Homeland Security (DHS) has provided no public evidence of that link.
Still, DHS recently warned of “credible threats” to ICE and Customs and Border Protection (CBP) personnel, citing intelligence that criminal organizations have sought to pay for agent identities. Mexican President Claudia Sheinbaum dismissed those claims, saying no such bounty evidence has surfaced and that the U.S. had not shared any intelligence with them.
Pattern of Escalation
This is the latest in a series of leaks targeting ICE and related agencies. Earlier this year, details of planned ICE raids in Los Angeles were exposed online, prompting a DOJ investigation. In 2024 and 2025, Anonymous and other hacktivists released data tied to immigration enforcement and posted flyers naming ICE and HSI agents in Southern California.
The difference this time, analysts say, is scale and visibility. “Publishing hundreds of names tied to law enforcement crosses into physical-security territory,” said one federal cybersecurity source.
Government and Tech Response
The DOJ and DHS have launched investigations, while tech companies have been asked to remove online groups promoting or sharing the leaked data. Some ICE field officers have reportedly begun wearing masks during arrests to protect their identities.
Proposed legislation in Congress would make publicizing law enforcement officers’ personal data a felony if done with intent to obstruct investigations or incite harm.
Why It Matters
The breach highlights the growing overlap between hacktivism, criminal exploitation, and disinformation. It also shows how thin the line has become between digital breaches and real-world danger for those enforcing federal law.
Cyber experts warn that future leaks may grow even more sophisticated and that “The Com” may already have more sensitive data waiting to drop.
Bottom line:
The October doxxing campaign underscores a chilling reality … America’s law enforcers are becoming targets not just in the field, but online. And the threat isn’t purely technical. It’s human.